This July, we're launching the new version of our newsletter — now more complete than ever!
Just as cybersecurity continues to advance at a rapid pace, we too evolve and adapt to bring you the most up-to-date information possible. So, what can you expect in En la brecha? Timely insights on vulnerabilities, news, cybersecurity myths, and brand-new sections designed to keep you informed. We want this cybersecurity newsletter to become your trusted resource for staying one step ahead.
Welcome to the new edition...
 Monthly TOP
Monthly TOP
 WATCH OUT
WATCH OUT

In recent years, ransomware has seen an alarming rise, affecting organizations across various sectors worldwide. This type of cyberattack, in which attackers encrypt critical data and systems and then demand a ransom for their release, has become one of the greatest threats to cybersecurity.
One of the most impacted sectors is transport and logistics, as demonstrated by the recent incident suffered by OCASA. This attack took down their website and disrupted services, highlighting the sector’s vulnerability to this specific threat.
Ransomware is especially damaging for these organizations due to its ability to paralyze critical operations. Such disruptions can impact the supply chain, causing delivery delays, financial losses, and damaging customer and partner trust.
 TOP NEWS
TOP NEWS

Spanish Port System Increases Its Cybersecurity Measures
The Smart Ports Chair highlights the importance of cybersecurity across Spain’s 46 state-owned ports to prevent economic and logistical impacts caused by cyberattacks. They advocate for a common cybersecurity services platform and a Security Operations Center (SOC), aiming to streamline management and enhance the resilience of the ports.

Cyberattack on France's Railway Network During the Olympic Games
Paris has suffered a cyberattack that has paralyzed a large part of France's high-speed railway network, affecting three of the four main TGV lines heading to the French capital. This has left 800,000 travelers stranded and caused a major uproar on the opening day of the Paris 2024 Olympic Games.

Chronology of the CrowdStrike Update Failure on Windows
To understand the incident of the failed CrowdStrike update that caused Blue Screens of Death (BSOD), we provide a chronology of the events. We will analyze the impact on various industries and regions, the measures taken before and after, and the attacks that attempted to exploit the vulnerability.
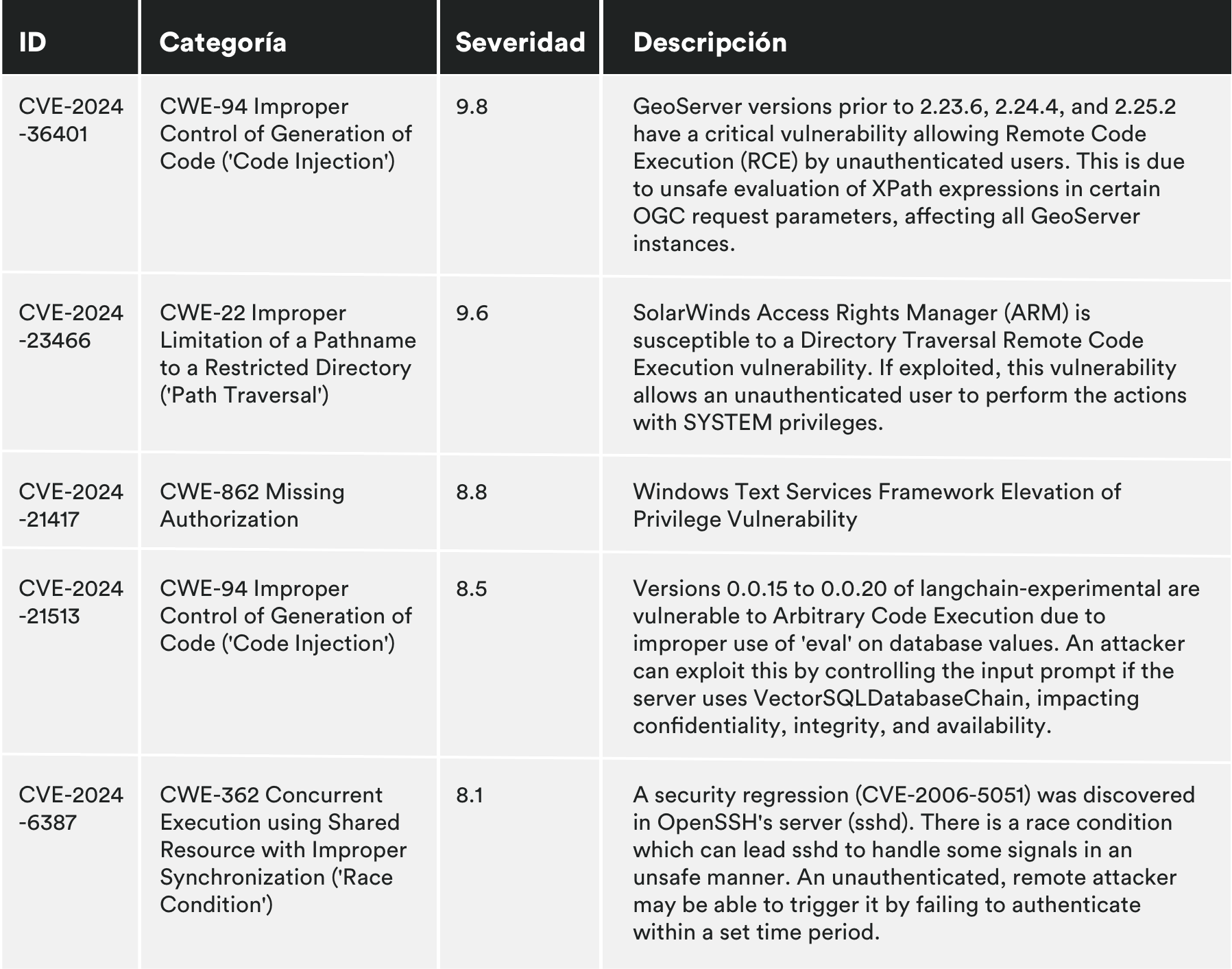
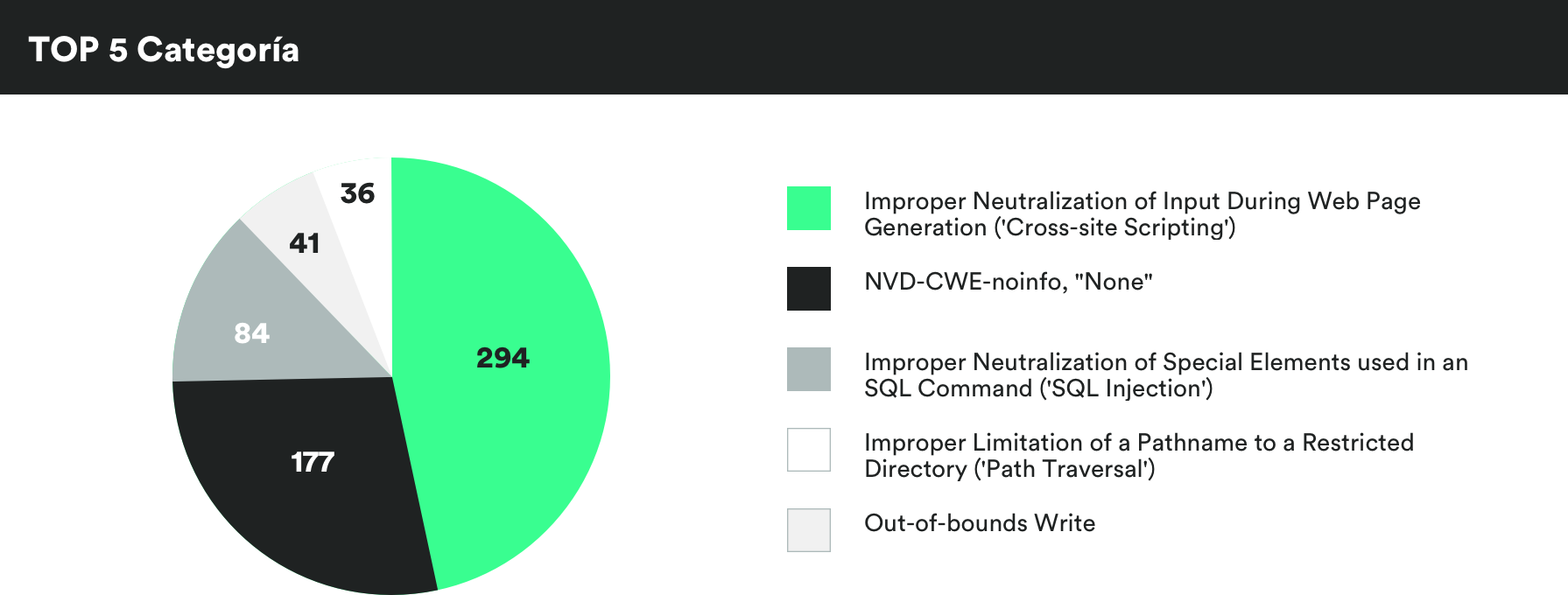
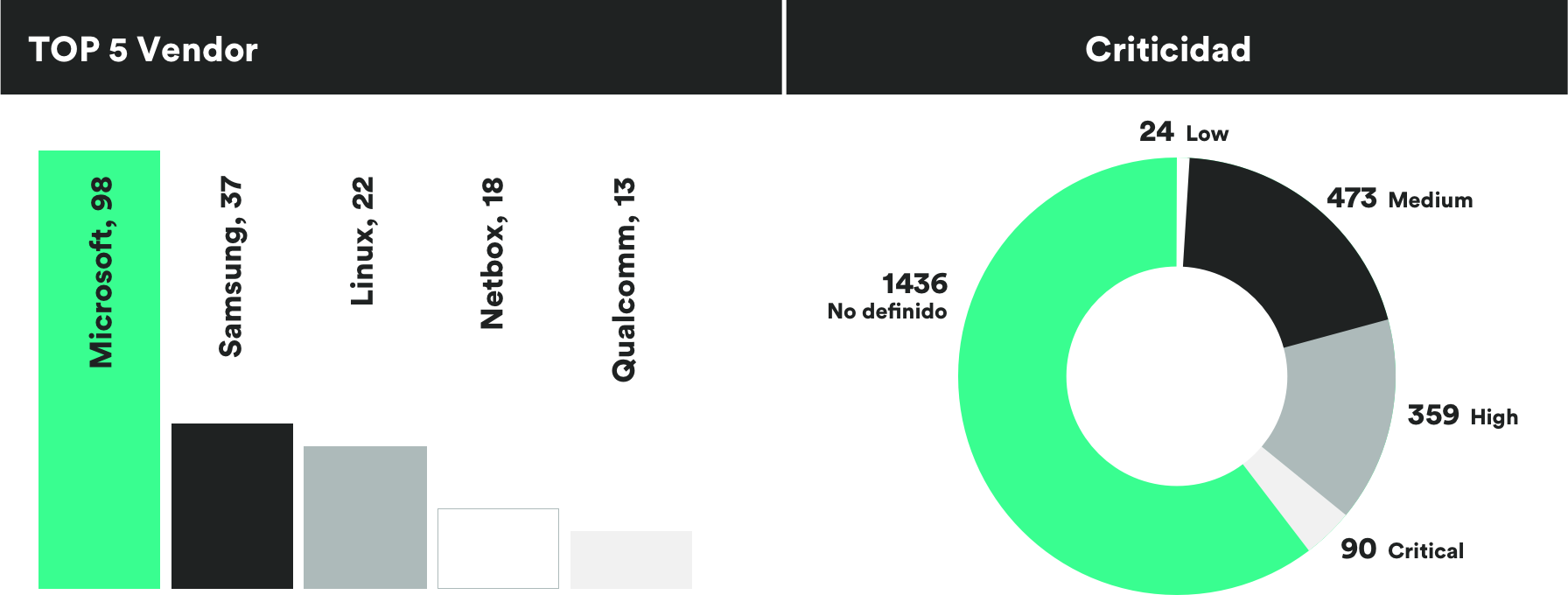
 MONTHLY VULNERABILITIES
MONTHLY VULNERABILITIES
 DEBUNKING MYTHS/CURIOSITIES
DEBUNKING MYTHS/CURIOSITIES
"Cyberattacks can only occur through the Internet"
arise from multiple sources.
Insider attacks are carried out by individuals within the organization, such as employees inserting infected USB devices into internal systems. Zero-day attacks exploit unknown vulnerabilities in software or hardware and can originate in various ways, not just online. Social engineering, through techniques like phishing, manipulates people to gain access or confidential information, demonstrating that the Internet is not always needed to launch an attack.
Organizations must implement comprehensive security measures, educate staff, and enforce strict security policies to protect against all potential threats. Recognizing that cyberattacks can come from multiple vectors is crucial for an effective security strategy.
 REVIEWING CONCEPTS
REVIEWING CONCEPTS
What is Spoofing?
Spoofing is the technique through which an attacker can impersonate specific information with the goal of impersonating an identity to deceive a system, person, or device.
Any value that allows for the validation of an association—in this case, we are talking about the association between a person and a system—can be susceptible to this type of attack technique. However, it’s important to remember that spoofing is not necessarily used to impersonate a person. For example, it can also be used to impersonate a machine that is only supposed to communicate with another.