MONTHLY TOP
 WATCH OUT
WATCH OUT

Cyberattacks on the supply chain have surged, with nearly 50,000 new victims in this latest period alone. Attackers are exploiting vulnerabilities in suppliers to infiltrate the systems of large companies, even impacting critical infrastructure. The most concerning aspect is that these infiltrations are difficult to detect, as they come from the same suppliers that are blindly trusted.
Now is the time to step up and review how you manage security with your business partners. Constantly auditing suppliers and strengthening your control measures is key to keeping your systems safe. Always keep your security protocols updated and ensure that the third parties you work with do the same.
 FEATURED NEWS
FEATURED NEWS

Anatomy of a Cyberattack: "If You Lose Your Calm, You Lose Everything"
INCIBE explains how to face a cyberattack through a targeted ransomware simulation. It emphasizes the importance of staying calm and following a crisis management plan, highlighting that losing your composure can worsen the situation. It also underscores the importance of collaboration and information sharing between companies to improve the response to cyber threats.

Transposition of the NIS2 Directive, Key Aspects to Consider
The transposition of the NIS2 Directive will impact companies in Spain, specifically in cybersecurity. Companies categorized as essential or important will need to comply with stricter regulations to prevent cyberattacks and manage incidents efficiently. Additionally, recommendations are provided on how to prepare for these new obligations and avoid penalties.

Cybercriminals Use Fake CAPTCHAs to Infect with Malware
How cybercriminals are using fake CAPTCHAs to infect millions of devices with malware, the tactics these attackers employ to deceive users into believing they are completing a legitimate security verification. By interacting with these fraudulent CAPTCHAs, users unknowingly download and install malicious software.
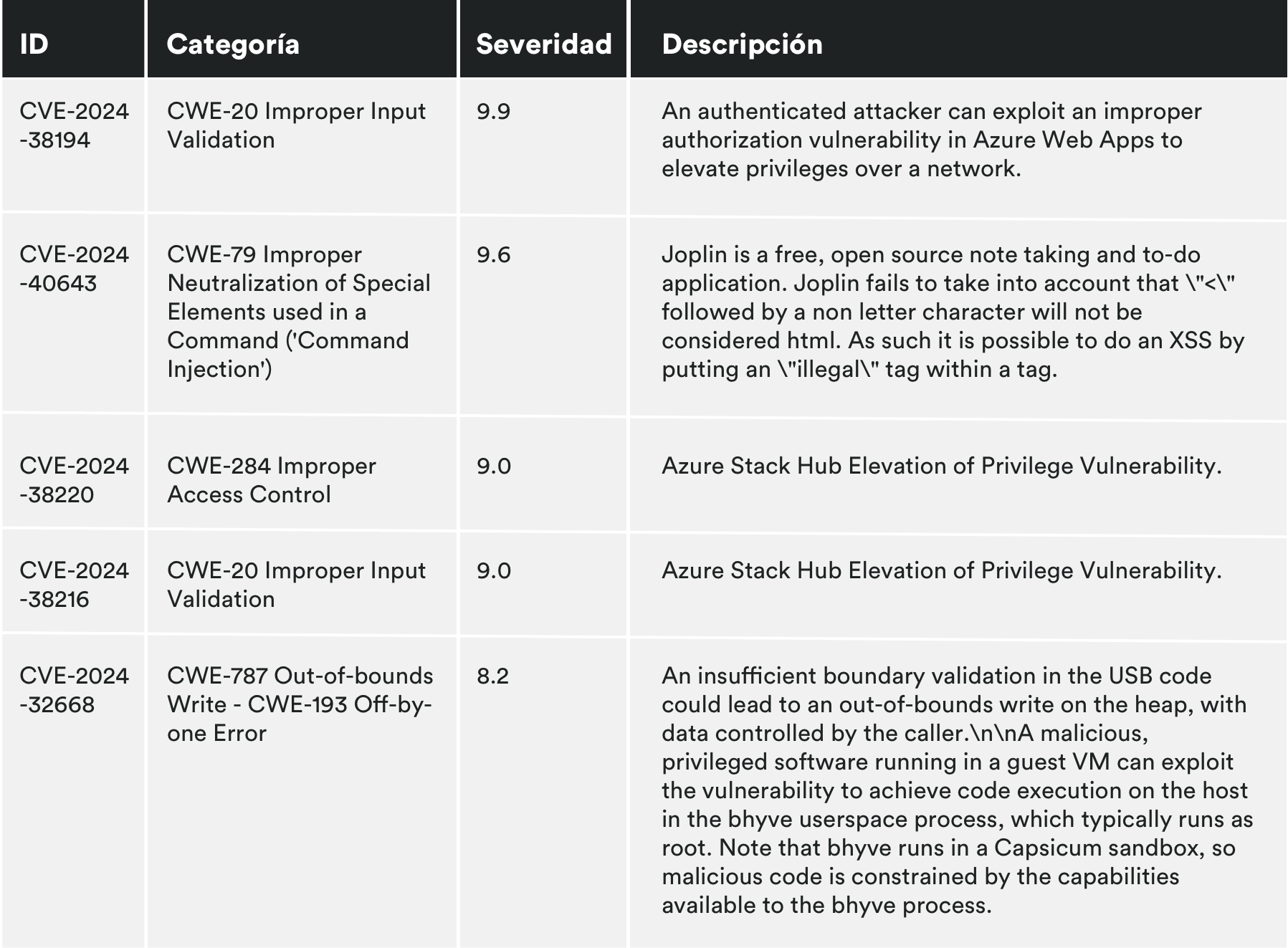
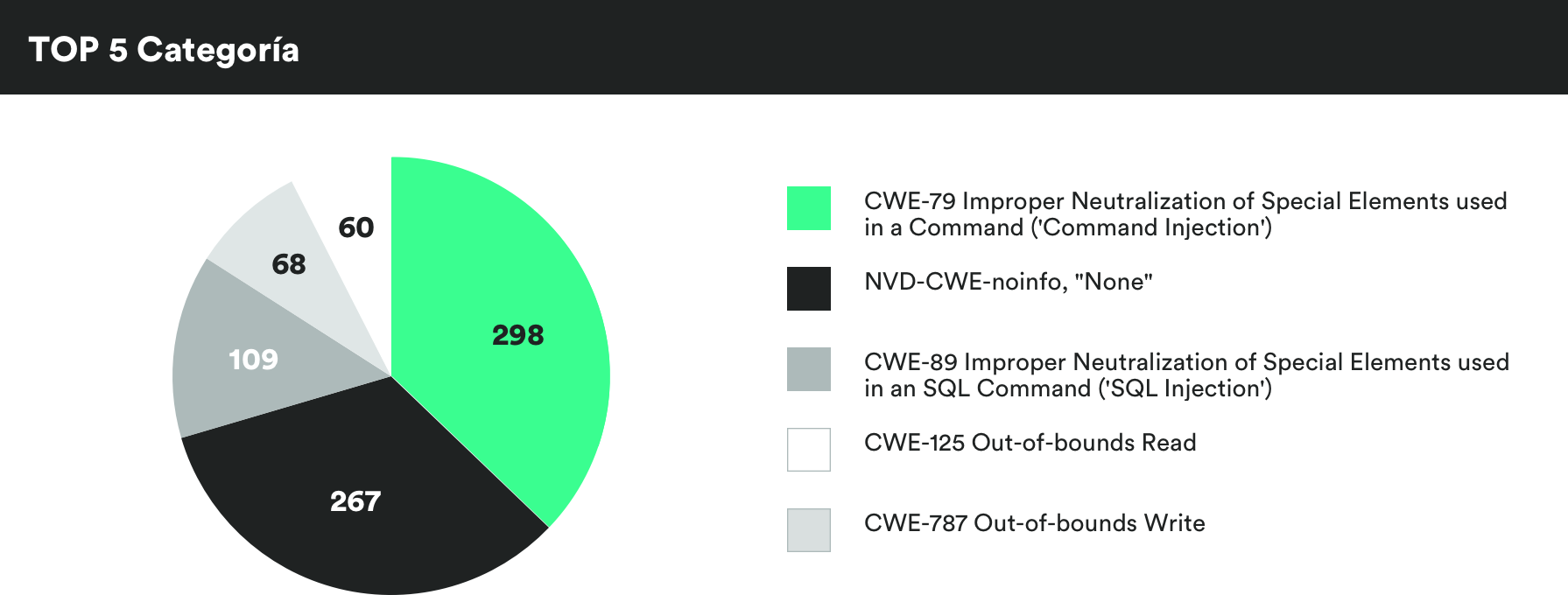
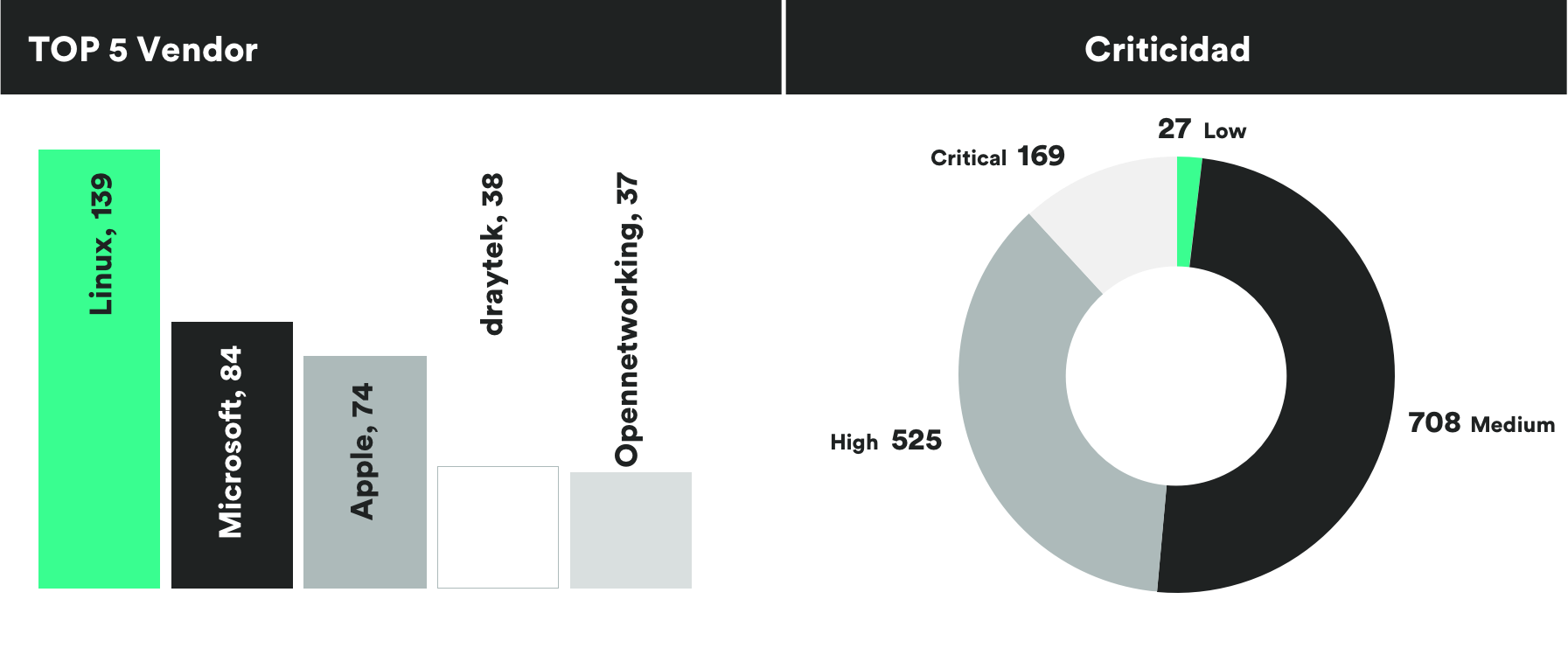
 MONTHLY VULNERABILITIES
MONTHLY VULNERABILITIES
 I LAUGH BECAUSE I DON´T WANT TO CRY
I LAUGH BECAUSE I DON´T WANT TO CRY
The Day Dallas Thought the Apocalypse Was Coming (or Almost)
One Ordinary Night in 2017 in Dallas, everything was calm... until suddenly, 156 emergency sirens began blaring as if a tornado was about to wipe the city off the map. What was the cause? No, it wasn't a natural disaster or an alien invasion... it was a cybercriminal deciding to have some fun. Yes, that's how it happened!
The siren system in Dallas, which operated via a radio frequency system, was misconfigured and lacked proper authentication measures to prevent unauthorized access. This allowed the attacker to intercept the control signal and remotely activate the sirens. By compromising the communication channel, the attacker managed to trigger chaos without needing physical access to the infrastructure, exploiting vulnerabilities in the system’s remote control.
The best (or worst, depending on how you look at it) part is that the attack wasn't even sophisticated. An amateur cybercriminal achieved what even tornadoes couldn't: causing panic across the entire city! Lesson learned and ears recovered, fortunately!
 HIGHLIGHTED EVENTS
HIGHLIGHTED EVENTS
