MONTHLY TOP
 WATCH OUT
WATCH OUT
Increase in Mobile Banking Trojans Targeting Financial Institutions
Recently, there has been an increase in the activity of banking trojans designed for mobile devices, such as FakeCall, affecting Android users. This malware masquerades as legitimate banking apps and, once installed, can intercept calls, messages, and credentials, allowing attackers to access bank accounts and perform fraudulent transactions. Additionally, these trojans can hijack communications between the client and the financial institution, making it harder to detect malicious activities.
Recommendations:
- Strengthen mobile app security: Implement robust multi-factor authentication and advanced malware detection techniques to identify suspicious behaviors in real-time.
- Continuous transaction monitoring: Use analytics systems to detect unusual transaction patterns and alert about possible fraudulent activities.
- Education and awareness: Conduct informational campaigns directed at customers about the risks of downloading apps from unofficial sources and the importance of keeping their devices updated.
- Inter-institutional collaboration: Share information about emerging threats with other financial entities and cybersecurity organizations for a coordinated and effective response.
 FEATURED NEWS
FEATURED NEWS

The Biggest Cryptocurrency Heist in History Hits Bybit: $1.5 Billion
Bybit has suffered the largest cryptocurrency heist to date, losing $1.5 billion in Ethereum following a cyberattack attributed to the North Korean group Lazarus. The platform assures that user funds are protected.
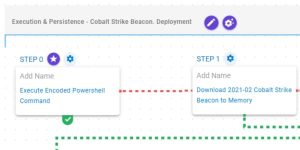
Ransomware Ghost / Cring in Latin America
The Ghost ransomware (Cring) remains active and has targeted organizations in over 70 countries, including Latin America. It exploits vulnerabilities in outdated software such as Fortinet and Microsoft Exchange to infiltrate and encrypt data. Authorities urge updating systems and strengthening security.
La novedad que prepara Google para luchar contra las estafas: adiós a la autenticación de seis dígitos por SMS
Google reemplazará la autenticación en dos pasos por SMS con códigos QR en Gmail para mejorar la seguridad y evitar estafas. Esta medida busca reducir el riesgo de interceptación de códigos y fortalecer la protección de las cuentas.
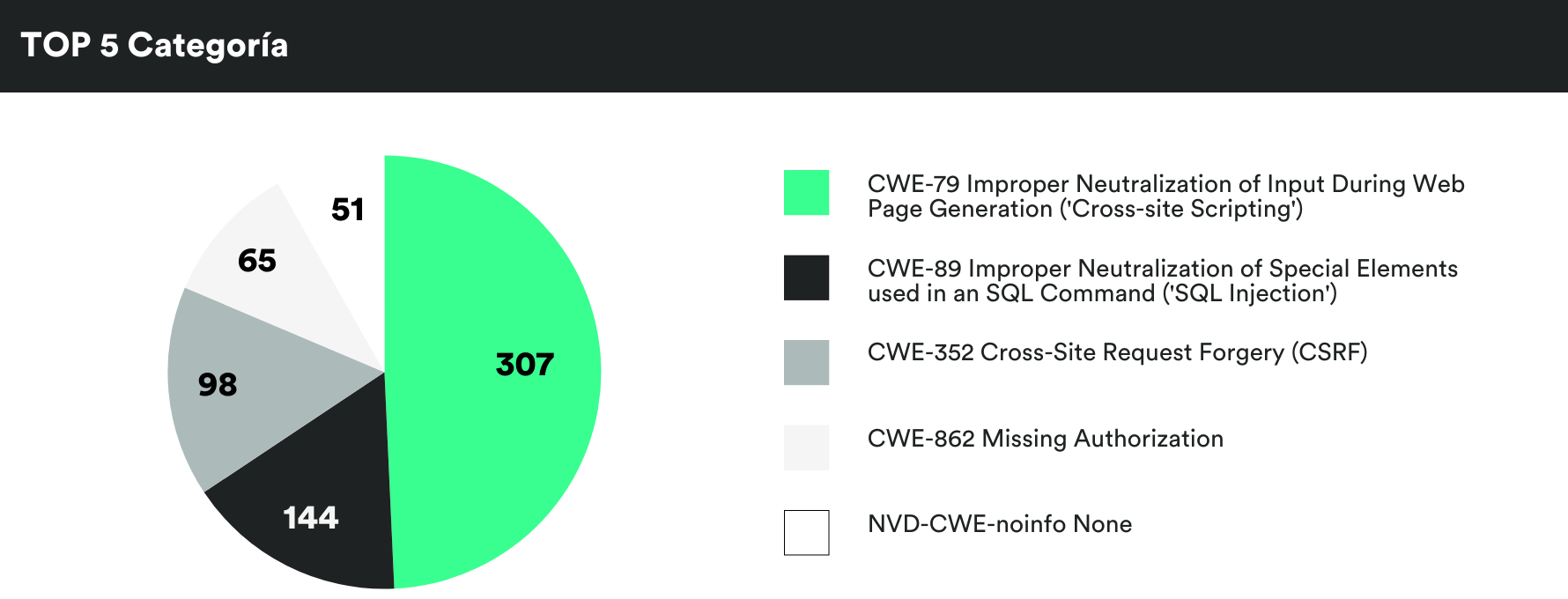
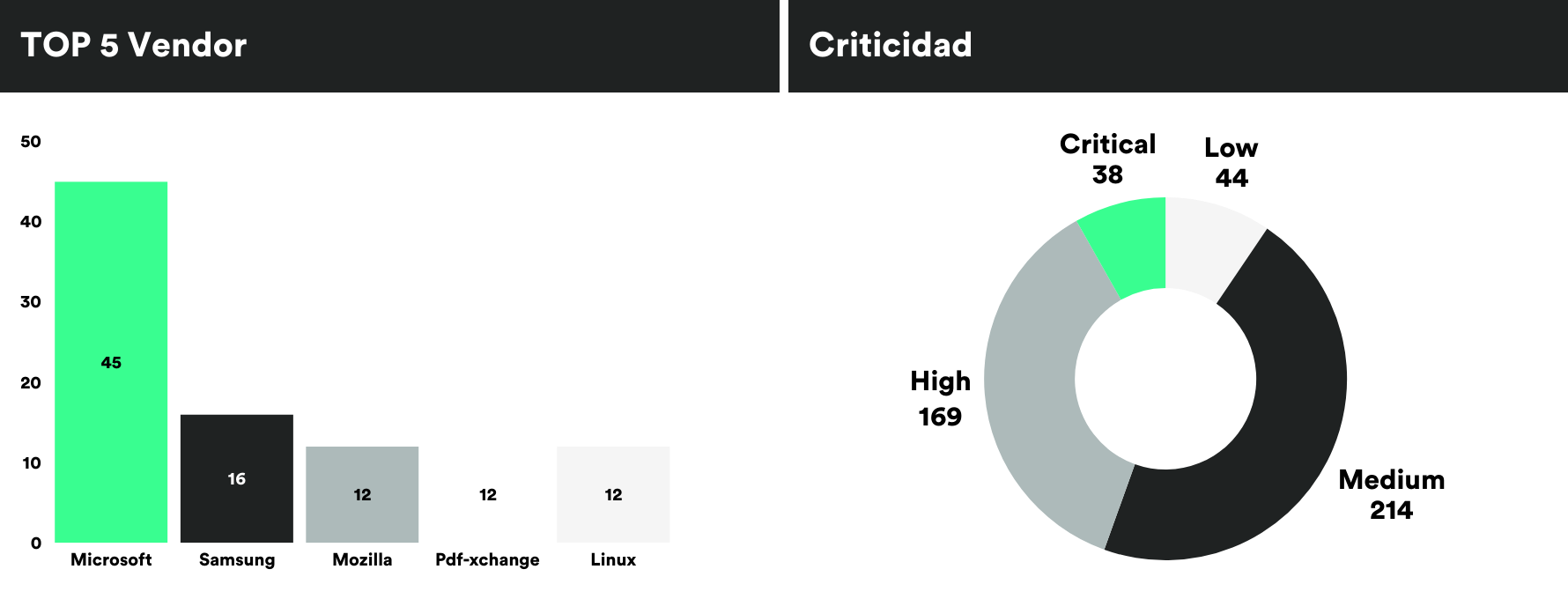
 MONTHLY VULNERABILITIES
MONTHLY VULNERABILITIES

 DEBUNKING MYTHS/CURIOSITIES
DEBUNKING MYTHS/CURIOSITIES
"Cybersecurity is only the responsibility of the IT team"
It’s a mistake to think that cybersecurity is solely the responsibility of the IT team. In reality, the weakest link in the security of any organization is often the human factor, not the technology.
Phishing attacks, the use of weak passwords, downloading malicious files, or accessing unsecured networks are just a few examples of how employees, unknowingly, can compromise the company’s security.
Security must be a joint effort throughout the organization:
- Ongoing training
- Clear security policies
- Multi-factor authentication (MFA)
- A security culture
It doesn’t matter how advanced the technology is if people don’t know how to protect themselves. Security is everyone’s responsibility.
 TIP OF THE MONTH
TIP OF THE MONTH
Compromised credentials are the gateway to many cyberattacks. A secure password is not enough; you need to go further.
