 MONTHLY TOP
MONTHLY TOP
 PHISHING WITH AI: THE RISK THAT COULD COMPROMISE YOUR ORGANIZATION
PHISHING WITH AI: THE RISK THAT COULD COMPROMISE YOUR ORGANIZATION

Artificial intelligence is not only transforming business technology but also the tactics of cybercriminals. One of the most recent threats is the use of AI to clone voices and personalize phishing attacks targeting key employees in companies. Imagine your CFO receives an urgent call from a "CEO" requesting approval for a transfer. The concerning part: it seems completely real.
What can you do as a CISO?
- Establish verification protocols: Ensure that all sensitive requests (such as money transfers) follow a multi-channel confirmation process.
- Enhance training: Educate your team on these new tactics and how to detect them.
- Audit internal communications: Identify potential vulnerabilities in communication flows that could be exploited.
Cybercriminals are using increasingly advanced tools, but with proactive measures in place, you can keep your team one step ahead.
 FEATURED NEWS
FEATURED NEWS

OtterCookie, the espionage tool putting global cybersecurity at risk
A new malware, named OtterCookie, is being used by actors linked to the North Korean government in a campaign targeting developers and tech companies. This attack exploits tools like Node.js and npm packages to infiltrate systems and steal critical information, such as credentials and financial data.

AI in Cybercrime: Language Models Amplify Phishing Scams
AI is changing the game in cybercrime. Attackers are using advanced language models to make phishing scams more convincing and harder to detect. This approach not only puts unsuspecting employees at risk but also poses a significant challenge for traditional detection tools.

Cyberattack: The 'Cryptoransomware' That Has Threatened National Security
The cryptoransomware Trinity has put the Tax Agency at risk, encrypting data from millions of taxpayers. The attackers are demanding a ransom in cryptocurrency, threatening to release the information if payment is not made by December 31. This incident highlights the urgency of strengthening cybersecurity in public institutions.
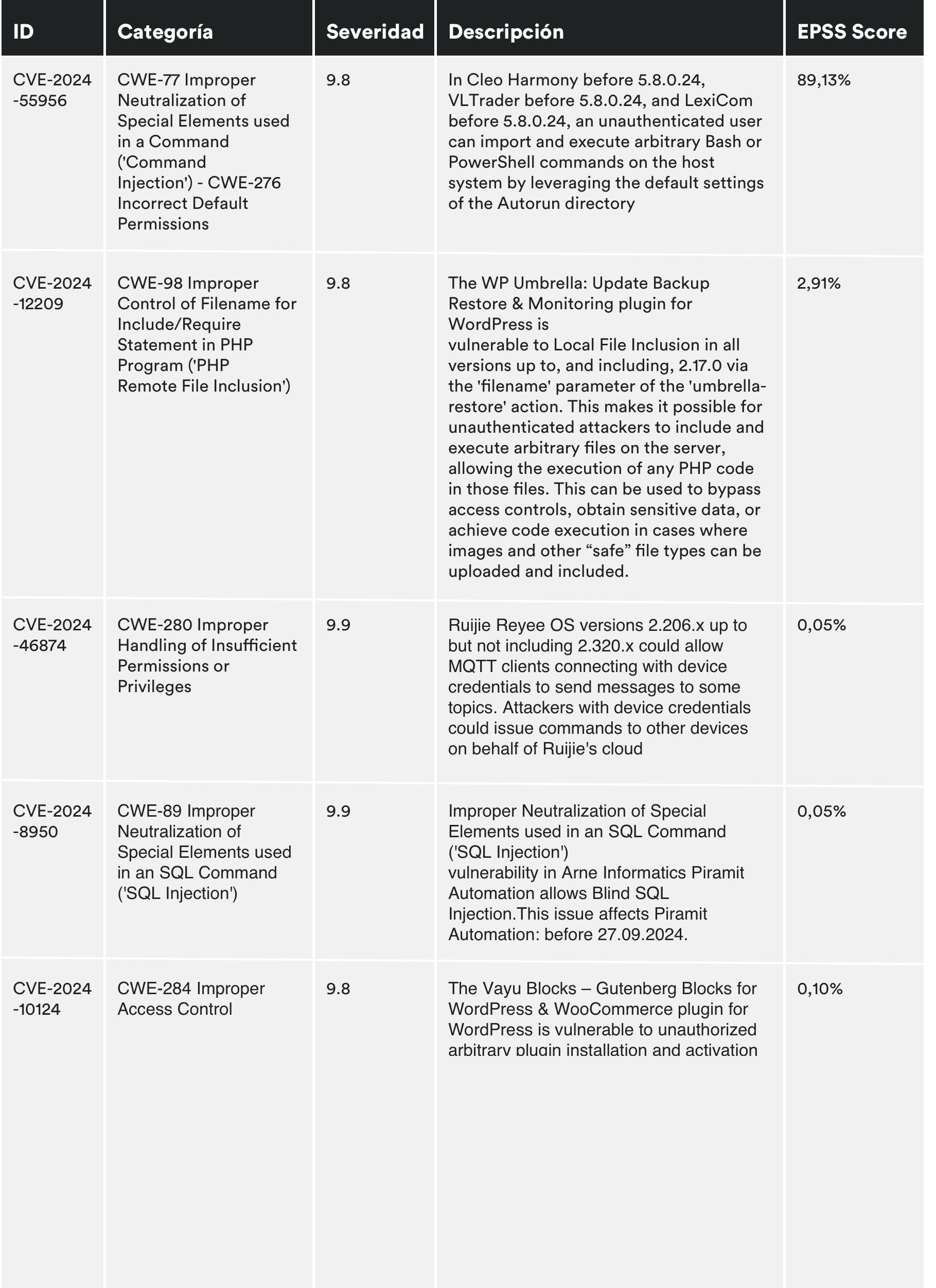
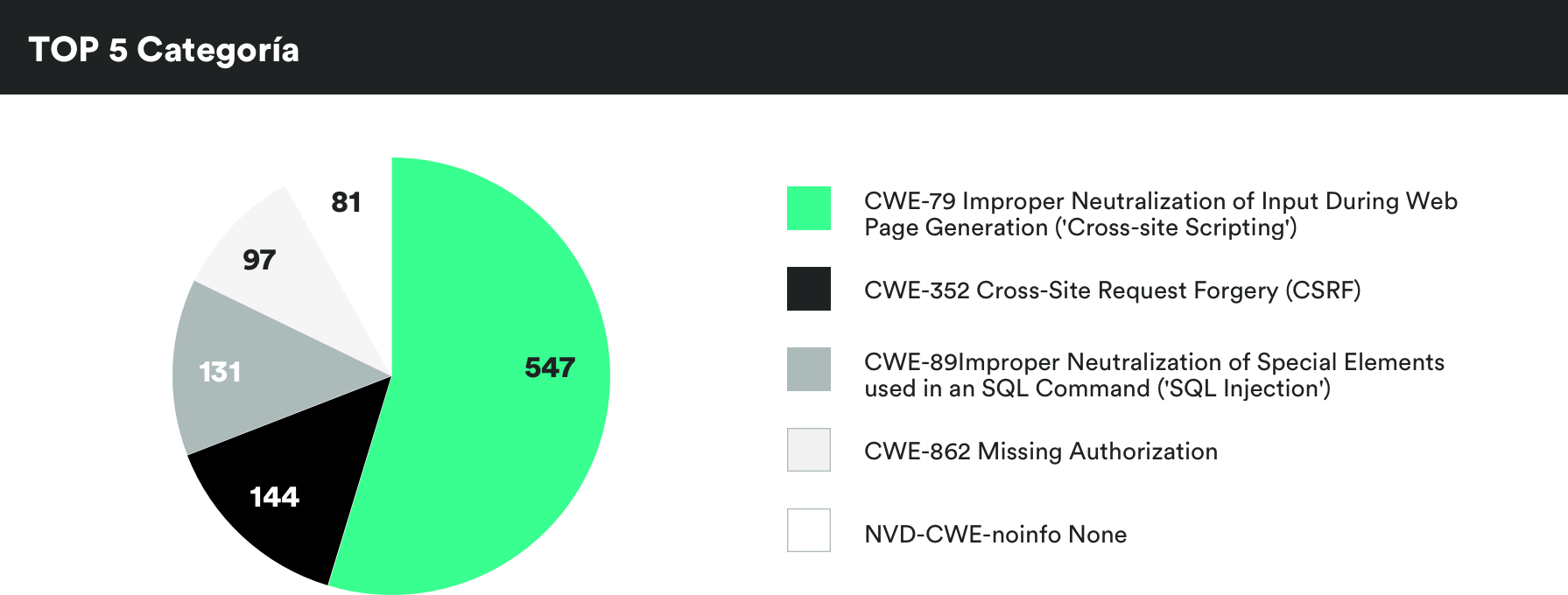
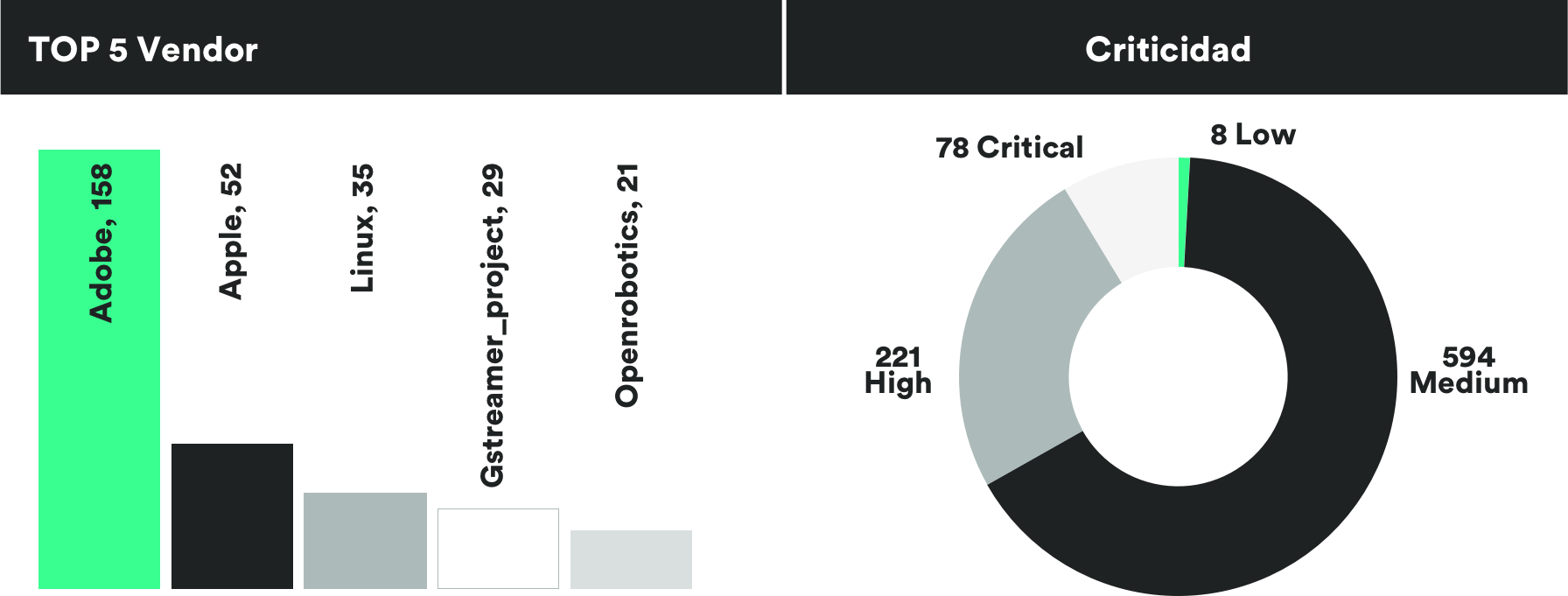
 MONTHLY VULNERABILITIES
MONTHLY VULNERABILITIES
 DEBUNKING MYTHS / CURIOSITIES
DEBUNKING MYTHS / CURIOSITIES
"IoT devices are not a risk to businesses"
In many companies, IoT devices such as cameras, HVAC systems, or sensors often go unnoticed during security audits. The mistaken belief that they are just "connected tools" leads to these devices being ignored as potential attack vectors.
IoT devices are small computers with operating systems, open ports, and often default passwords that are never changed. This makes them the perfect target for cybercriminals, who use them to infiltrate networks, launch Distributed Denial of Service (DDoS) attacks, or even spy on business activities.
What you need to know:
- IoT devices have been used in major attacks, such as the infamous Mirai botnet case, which compromised millions of devices to take down global websites.
- Without proper isolation, a compromised IoT device can serve as an entry point into critical systems.
- Many companies fail to update the firmware of these devices, leaving open vulnerabilities that have already been discovered.
IoT devices are not harmless. Ignoring them in your cybersecurity strategy is like leaving a window open in a house protected by steel doors. Include them in your audits, apply access controls, and segment networks to prevent what seems harmless from becoming a critical threat.
 I LAUGH BECAUSE I DON'T WANT TO CRY
I LAUGH BECAUSE I DON'T WANT TO CRY
A virus with a budget-saving agenda... the whole budget
Imagine you're in charge of the budget for an entire country, and suddenly, poof, it's gone. No, it's not a magic trick; it's a computer virus. In 2003, Ukraine experienced this bizarre incident when a cyberattack wiped out its national budget, leaving the country in something like "extreme savings mode"... because they literally no longer knew how much money they had.
This event not only gave the government a major headache, but also demonstrated what happens when you trust your 1998 antivirus more than actual cybersecurity measures. The moral of the story? It's always better to have a backup, because while hackers don’t respect budgets, financial problems don’t wait either.