 MONTHLY TOP
MONTHLY TOP
 WATCH OUT FOR BLACK FRIDAY AND CYBER MONDAY
WATCH OUT FOR BLACK FRIDAY AND CYBER MONDAY

Big shopping days like Black Friday and Cyber Monday not only attract buyers looking for deals but also cybercriminals, who take advantage of the increased online activity to launch targeted attacks. During these periods, the risk of phishing, malware, and unauthorized access skyrockets, both for consumers and organizations.
Make sure your business isn’t the “discount” the attackers are looking for with these key measures:
1.Reinforce training: Educate the team about the risks of fraudulent emails and links.
2.Monitor traffic: Control remote access and detect suspicious activities.
3.Secure remote access: Review VPN configurations and external device setups.
4.Update systems: Apply the latest patches to all critical platforms.
5.Implement MFA: Add multi-factor authentication to key access points.
6.Simulate attacks: Run internal tests to identify weak points.
7.Protect data: Encrypt sensitive information and set up fraud alerts.
Security never takes a break, especially during high-activity days like these. Get your organization ready to stay one step ahead!
 FEATURED NEWS
FEATURED NEWS

Cybersecurity Investment Congress organized by CyberMadrid
Microsoft has launched Quick Machine Recovery, a tool to remotely repair Windows devices that do not boot correctly. This development responds to the July incident with CrowdStrike, when a faulty update affected millions of devices, causing global disruptions in critical sectors.

Microsoft introduces "Quick Machine Recovery" to prevent incidents
Microsoft has launched Quick Machine Recovery, a tool to remotely repair Windows devices that fail to boot correctly. This development responds to the July incident with CrowdStrike, when a faulty update affected millions of devices, causing global disruptions in critical sectors.

The largest CSIC center paralyzed by a cyberattack
The INIA-CSIC, the largest center of the CSIC, has been paralyzed by a ransomware attack that left 600 employees without access to the internet or key systems. The COCS is working on restoration while staff manage tasks manually, and investigations continue to determine the origin and mitigate its impact on ongoing research.
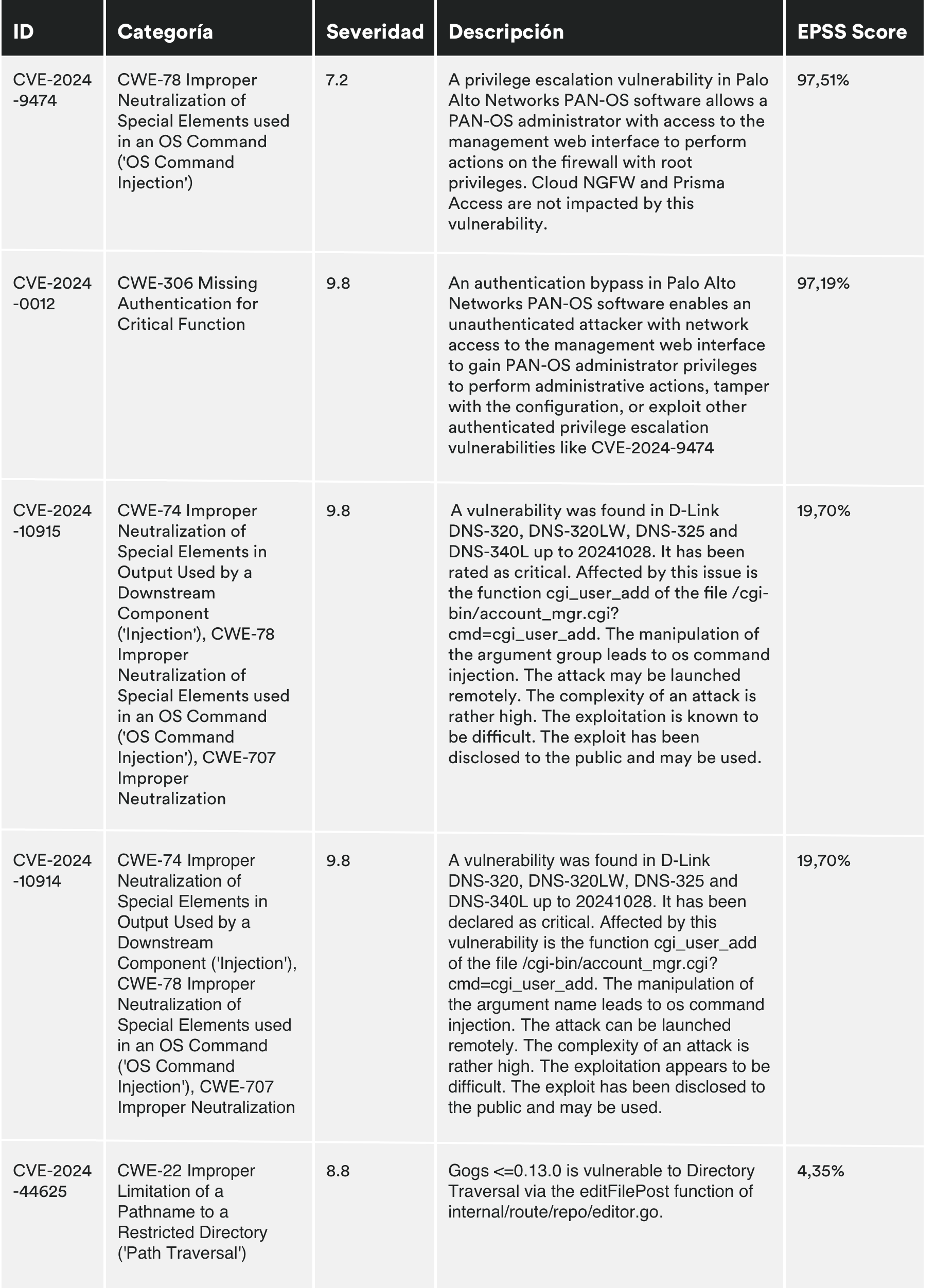
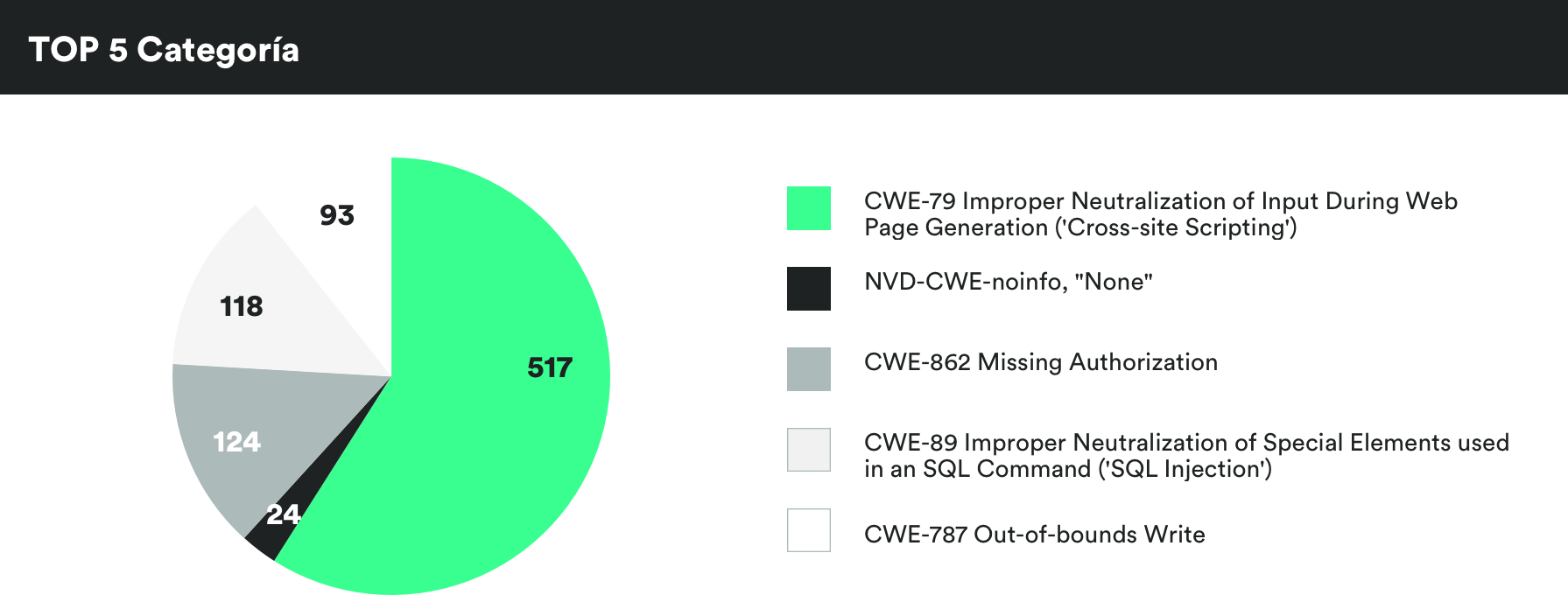
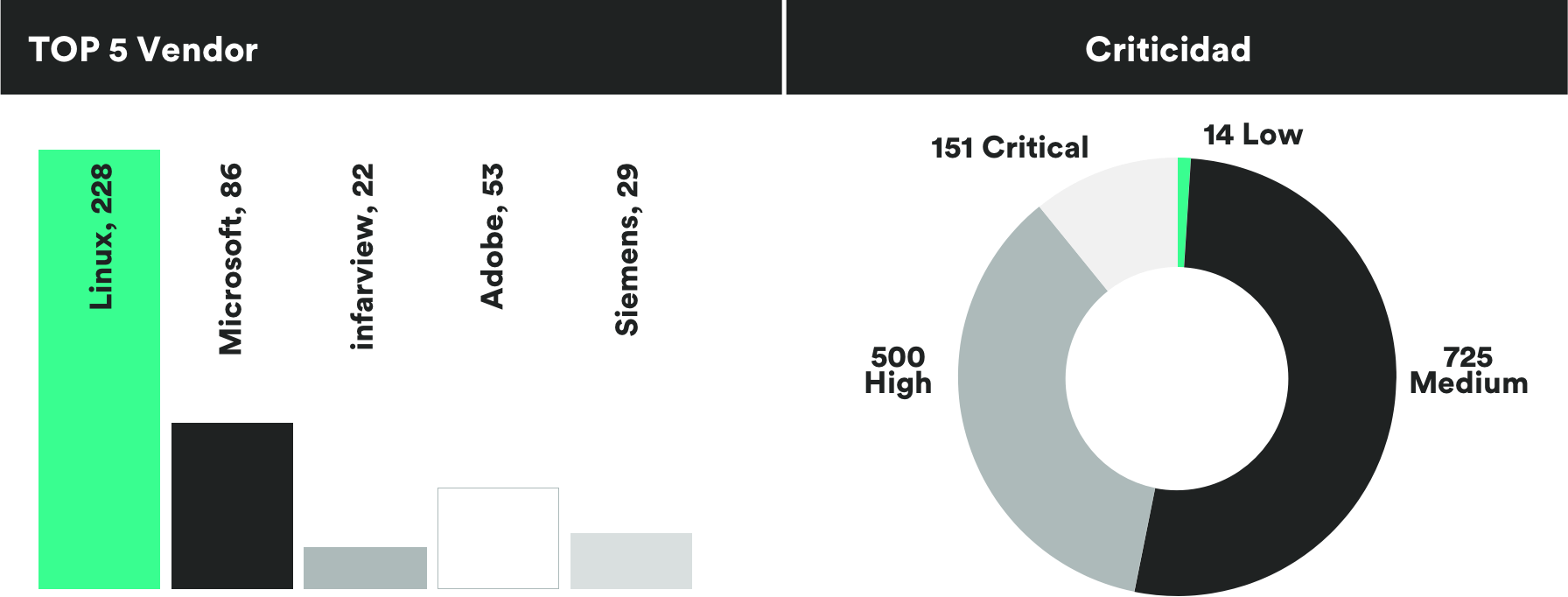
 MONTHLY VULNERABILITIES
MONTHLY VULNERABILITIES
 DEBUKING MYTHS /CURIOSITIES
DEBUKING MYTHS /CURIOSITIES
"There is no phishing beyond email"
We see how phishing has evolved into something much more sophisticated. Although email remains the most common channel, cybercriminals have expanded their reach through SMS (smishing), phone calls using AI to clone voices (vishing), and social media, multiplying the entry points to deceive employees and executives.
A text message asking you to "verify your account," a call pretending to be from technical support, or a malicious link on social media can be just as dangerous as a traditional phishing email. These attacks often stand out for their personalized and urgent tone, prompting victims to act without thinking.
Ongoing training and phishing detection tools across different channels are essential to protect organizations. For example, attack simulation technologies can help identify weak points and reinforce staff behavior against these threats. Because, in the end, phishing is not just an email: it's any door we leave slightly open.
TIP: If you have doubts about the message or its origin, you can verify it through another means with the sender of the email, message, or call, as well as carefully check the link it leads to, even before clicking.
 HIGHLIGHTED EVENTS
HIGHLIGHTED EVENTS
XVIII STIC CCN-CERT DAYS VI CYBERDEFENSE CONFERENCE: ESPDEF-CERT
From November 26 to 28, 2024
Kinepolis City of the Image (Madrid).

Organized by the National Cryptologic Center (CCN) and the Joint Cyber Space Command (MCCE), with the collaboration of RootedCON, this leading cybersecurity event in Spain brings together professionals from public administration, technology companies, academic institutions, and international organizations to discuss and share knowledge on threats, trends, and advances in cybersecurity.