MONTHLY TOP
 WATCH OUT
WATCH OUT

Public Wi-Fi networks, present in places such as cafes, airports, and shopping malls, offer convenience but also represent a significant attack vector. Cybercriminals can exploit these networks to carry out attacks such as Man-in-the-Middle (MitM), where they intercept and potentially alter communication between the user and the final destination.
Risks:
Data Interception
The lack of strong encryption in many public networks allows malicious actors to capture sensitive information transmitted, such as login credentials and financial data.
-
Malware Injection
Attackers can introduce malicious software into connected devices, exploiting vulnerabilities and compromising system integrity..
-
Fake Access Points (Evil Twin)
Cybercriminals create networks with names similar to legitimate ones to deceive users and gain unauthorized access to their devices.
Recommendations:
- Implementation of Network Usage Policies: Establish clear guidelines that discourage the use of public Wi-Fi networks for work-related activities without proper precautions.
- Mandatory VPN Usage: Ensure that all external connections go through a corporate Virtual Private Network to encrypt communication and protect data integrity.
- Disabling Automatic Connections: Configure corporate devices to avoid automatically connecting to available Wi-Fi networks, reducing the risk of insecure connections.
- Education and Awareness: Conduct regular informational sessions to help employees recognize and avoid threats associated with public networks, promoting safe browsing practices.
 FEATURED NEWS
FEATURED NEWS

Automation and Personalization Define the New Threat Landscape Facing Organizations
The 2025 Cybersecurity Trends Report by Sofistic points out that vulnerabilities have increased, but their severity has been reduced.

Warning of a Cyberattack on Google Chrome: A Phishing Campaign Allowed Spying on Our Computers
Chrome has been the victim of a phishing attack that sent malware in emails with the aim of infecting users' computers and spying on them.

The Director of INCIBE Describes the Chinese Artificial Intelligence DeepSeek as "A Weapon of Mass Destruction"
The Director of the National Institute of Cybersecurity of Spain (INCIBE), Félix Juárez, issued a warning on Tuesday about the dangers posed by Artificial Intelligence.
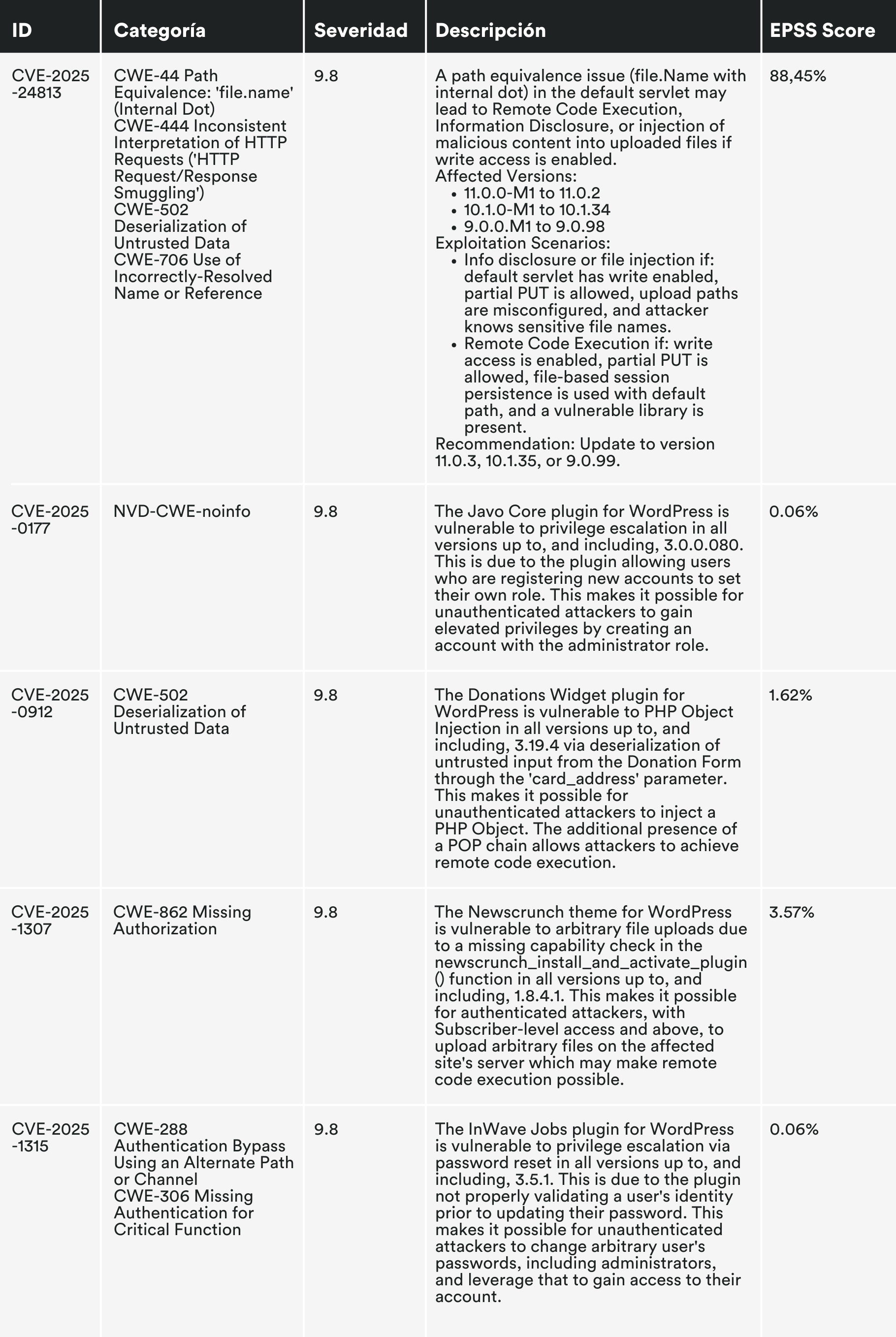
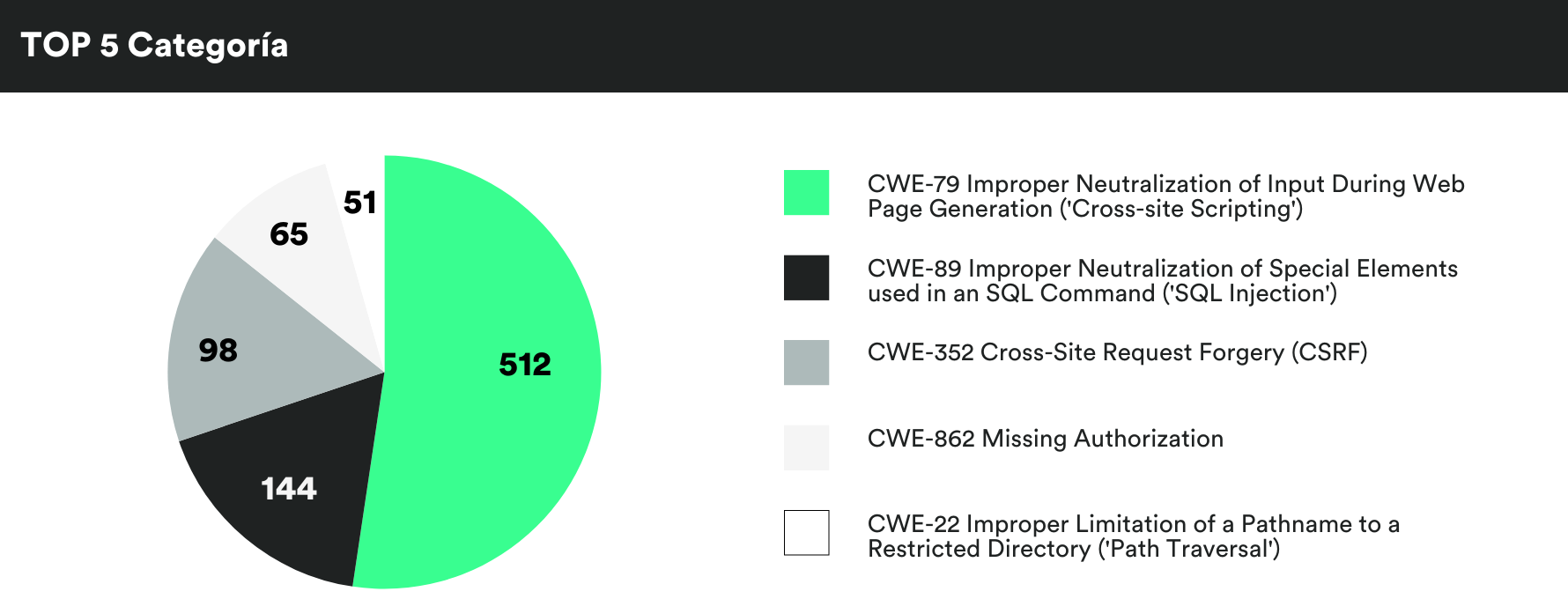
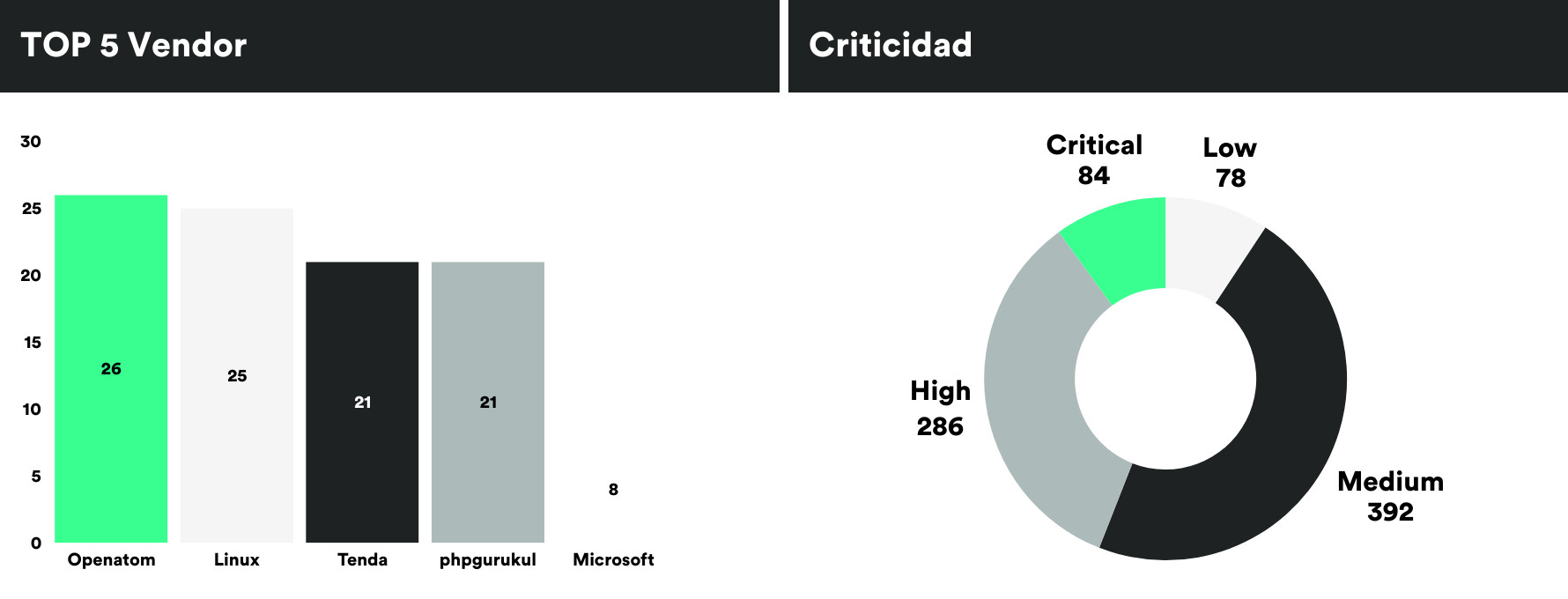
 MONTHLY VULNERABILITIES
MONTHLY VULNERABILITIES
 DEBUNKING MYTHS/CURIOSITIES
DEBUNKING MYTHS/CURIOSITIES
Is HTTPS = Secure Site? Spoiler: Not Always
For years, it has been repeated that if a website has the HTTPS lock, it is "secure." And yes, HTTPS ensures that the connection between your browser and the site is encrypted, but that doesn’t mean the website is legitimate or trustworthy.
In fact, currently, more than 80% of phishing sites use HTTPS with valid certificates. Why? Because today, obtaining an SSL/TLS certificate is fast, cheap (or free), and doesn’t require actual verification of the site's identity. Attackers take advantage of this to give fraudulent websites that clone banking entities, corporate networks, or well-known platforms a false sense of reliability.
Why does this matter? Because the lock gives a false sense of security. Many users see "https://" and assume the page is legitimate. And that’s where cybercriminals take advantage.
🔐 What should an organization do?
- Educate users: HTTPS only indicates encryption, not legitimacy. It’s important to teach how to identify suspicious URLs and avoid blindly trusting the lock.
- Simulate HTTPS attacks: Internal phishing exercises should include HTTPS pages so that employees don’t let their guard down.
- Implement proactive measures: DNS filtering, domain reputation analysis, and endpoint protection tools with real-time link verification.
Because in cybersecurity, as in life, not everything that shines (or everything with a lock) is secure.
 I LAUGH BECAUSE I DON'T WANT TO CRY
I LAUGH BECAUSE I DON'T WANT TO CRY
When a Click Turns Magic into a Nightmare
In the Disney universe, everything is magic… until you click where you shouldn’t. Just ask Matthew Van Andel, an engineer at the company, who downloaded an AI tool from GitHub without knowing it came with a gift: malware courtesy of the hacker group “NullBulge.”
The result? 44 million internal Slack messages leaked, personal data exposed, and chaos in Disney’s servers. But the story doesn’t end there: Matthew had his identity stolen and, to top it off, lost his job after inappropriate content was found on his work computer (he claims it was the malware, of course).
Moral of the story: not even in Disneyland are you safe if you don’t click wisely.
Does the HTTPS lock protect you from this? Spoiler: neither does magic.
