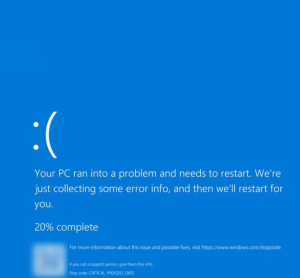
The main issue is that an antivirus (AV) needs access to information from other applications to function correctly and block them if it considers them fraudulent. In a very basic or primitive way, this is what an antivirus does. However, if in this process it blocks something essential for the proper functioning of the system, it can cause failures.
What happened with CrowdStrike is more complex, but this explanation is enough to understand why such incidents occur. For those who want a more technical explanation of what happened, I recommend this post by Sergio de los Santos on social media X.
First, let's list a series of cases where malware protection solutions have left their clients ‘stranded’ after an update. Surely there are many more, but these are the 7 cases that came to mind.
Soon, we will know how this was possible, because honestly, knowing the long history of similar failures from these kinds of companies, the volume of CrowdStrike’s customers, and the excellent work they’ve demonstrated over the years, it’s hard for me to believe that these processes didn’t exist.